The Evolution of Access Control Systems: From Keys to Biometrics
Access control systems are integral to security in both residential and commercial environments. Over the years, these systems have evolved significantly, transitioning from traditional key-based methods to sophisticated biometric solutions. This article explores this evolution, highlighting the benefits and advancements that each stage of development has brought to the field of access control.
1. Traditional Key-Based Access Control
For centuries, physical keys have been the standard for securing doors and restricted areas. This simple yet effective method provided a basic level of security, relying on the notion that only those with the physical key could gain access. However, traditional key systems have notable drawbacks:
- Vulnerability to Loss or Theft: Keys can be lost, stolen, or duplicated, posing significant security risks.
- Limited Tracking: Traditional keys do not offer any means of tracking who accessed an area or when.
- Inflexibility: Changing access rights requires rekeying locks, which can be time-consuming and costly.
2. Electronic Access Control Systems
The introduction of electronic access control marked a significant advancement in security technology. These systems utilize keypads, cards, and fobs, allowing for more flexible and secure access management. Key features include:
- Access Control Cards: Users are issued cards that can be easily programmed and deactivated, reducing the risk associated with lost keys.
- Keypads: PIN codes allow for quick access, but can be vulnerable to shoulder surfing and forgotten codes.
- Audit Trails: Electronic systems can log access events, providing insights into who accessed specific areas and when.
Despite their advantages, electronic systems still faced challenges, such as the potential for card cloning and the need for battery maintenance.
3. Smart Access Control Solutions
With the rise of smart technology, access control systems have evolved further to incorporate IoT (Internet of Things) capabilities. Smart locks and systems allow users to control access remotely via smartphones or web applications. Key benefits include:
- Remote Management: Users can grant or revoke access from anywhere, enabling greater flexibility and control.
- Integration with Other Systems: Smart access systems can be integrated with security cameras, alarms, and home automation for a comprehensive security solution.
However, these systems raise concerns about cybersecurity, as they may be vulnerable to hacking if not properly secured.
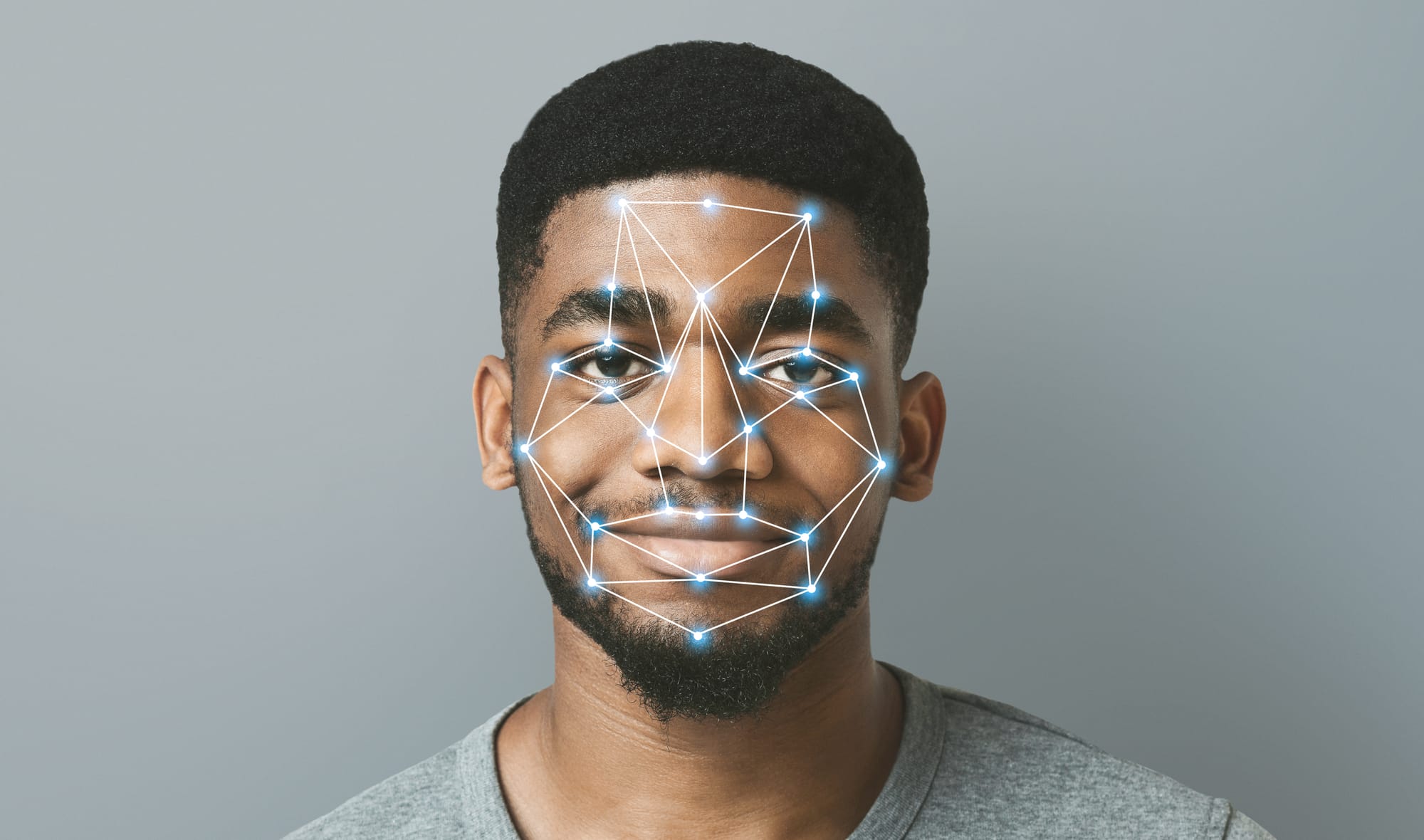
4. Biometric Access Control Systems
The latest evolution in access control technology is the rise of biometric systems. These solutions utilize unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to grant access. The key advantages of biometric systems include:
- Unmatched Security: Biometric identifiers are unique to each individual, making unauthorized access significantly more challenging.
- No Need for Keys or Cards: Users no longer need to carry physical tokens, reducing the risk of loss or theft.
- Enhanced Tracking and Accountability: Biometric systems provide accurate logs of who accessed a location and when, enhancing security oversight.
Despite their benefits, biometric systems are not without challenges. Concerns about privacy, data protection, and potential inaccuracies (e.g., false positives or negatives) must be addressed to ensure user trust.
5. The Future of Access Control
As technology continues to advance, the future of access control will likely see further innovations. Integration with AI and machine learning could enhance threat detection and user verification processes. Additionally, emerging technologies such as blockchain may offer secure ways to manage access credentials, further protecting sensitive information.
Conclusion
The evolution of access control systems from traditional keys to modern biometric solutions reflects the ongoing quest for enhanced security and convenience. As technology continues to advance, organizations and individuals can look forward to even more effective and secure access control measures that not only protect assets but also improve the overall user experience. Embracing these advancements is essential for staying ahead of security challenges in an increasingly complex world.


